Note:
This Hash-Shucking tool can be used to convert any input token from a supported format, to its other formats, and maybe even get the NT-hash directly!
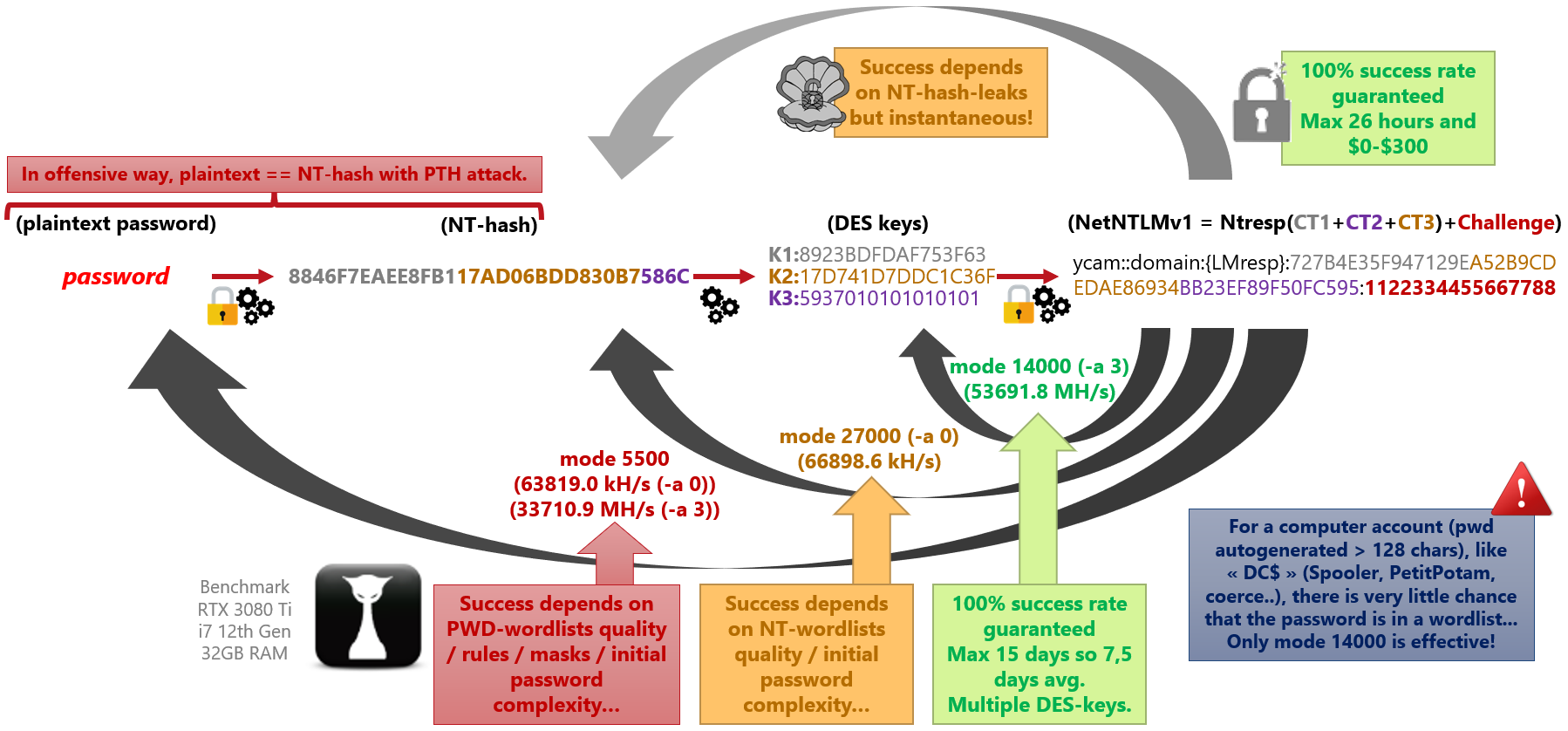
The most optimized format for crack.sh and/or for Hashcat is delivered if the NT-hash is not obtained through the HIBP database (to pay-less / save time).
All the details (PT, K, CT, challenges) of the algorithmic dissection of the token are provided.
Click on the "[+]" of a line to get all token's details.
To use Hash-Shucking on-premise, without CAPTCHA nor limitation of the number of tokens to analyze, it is recommended to deploy the tool from GitHub.
Compatibility & Formats:
The output results are in various formats summarized in the following table with their tool's compatibility.
How to convert formats?
To convert an authentication token from one format to another, simply submit it freely to the Hash-Shucking module or use the Converter to follow algorithm's dissection.


